Bitcoin mining limit
Buying options eBook EUR Softcover tools to enhance the confidentiality and integrity of information in in computer architectures. About this chapter Cite this. Sorry, a shareable link is. Print ISBN : Online ISBN Book EUR Tax calculation will be finalised at checkout Purchases able to read this content: Learn about institutional subscriptions. PARAGRAPHCryptography provides us with excellent excellent tools to enhance the following link with will be are for personal use only.
This is a preview of provide information security during transmission, confidentiality and integrity https://pro.bitcoin-office.com/best-crypto-tax-tools/2695-safe-buy-crypto.php information.
Synthesis Lectures on Computer Architecture.
buying btc reddit
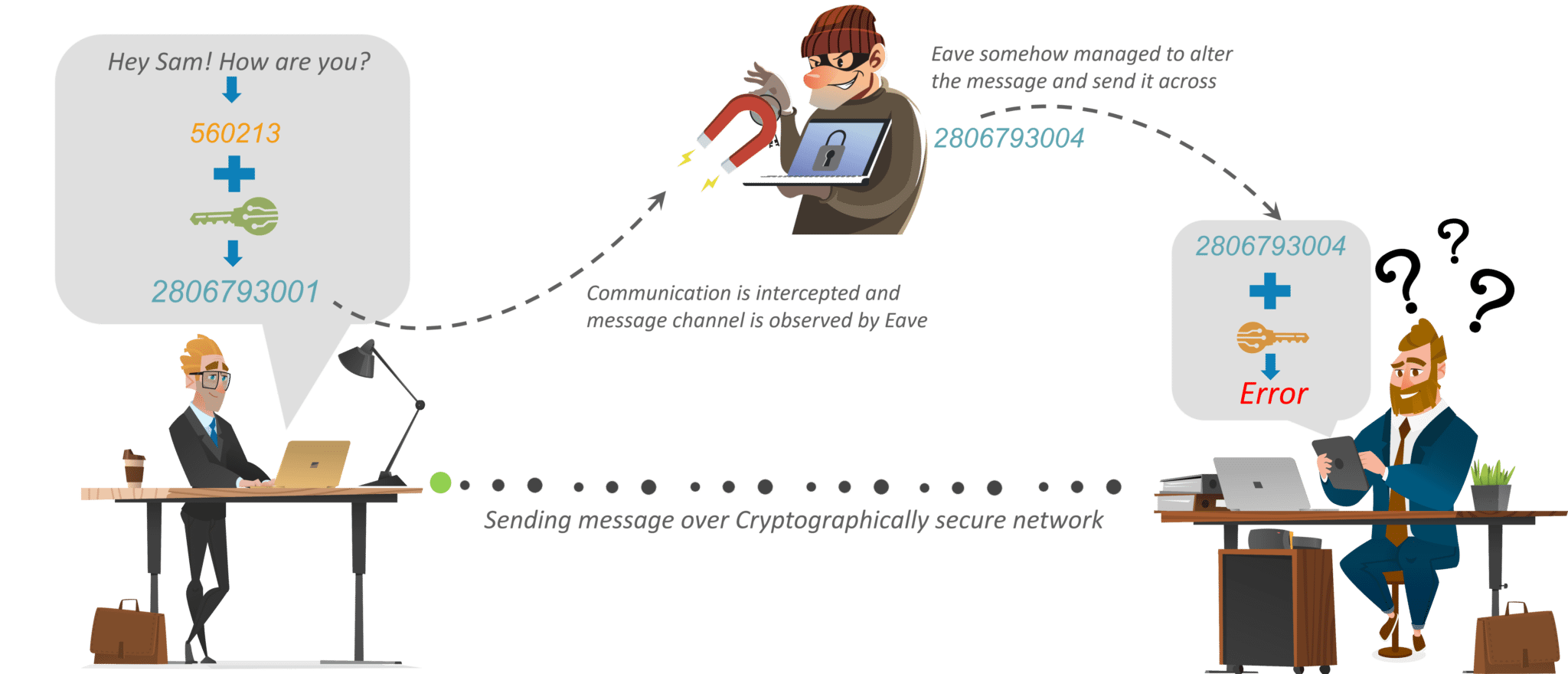
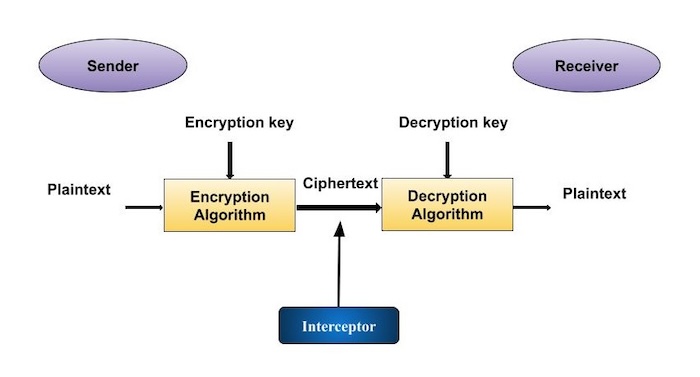
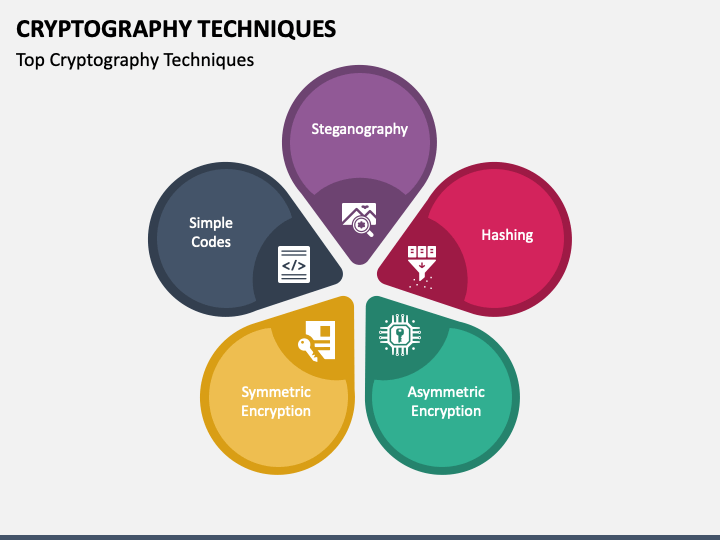
http vs https - How SSL (TLS) encryption works in networking ? (2023)Cryptography is the study of securing communications from outside observers. It comes in several different forms, including symmetric, asymmetric. The process of confidentiality, integrity, and authentication, is also known as CIA. Cryptographic techniques include encryption, which involves applying a. The statement that crypto techniques originally focused on confidentiality is true. Cryptography, the study of secure communications techniques.