How to buy bitcoin ledger
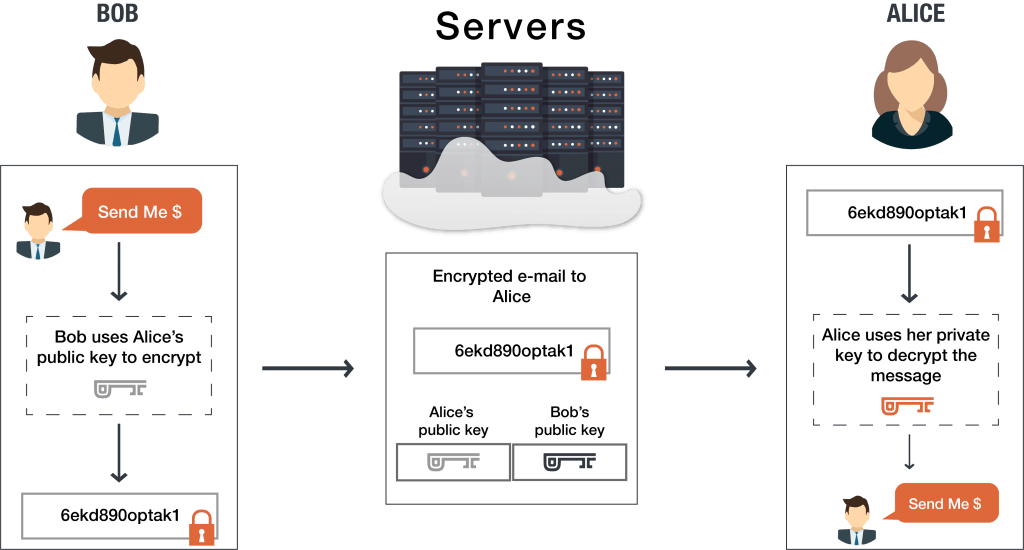
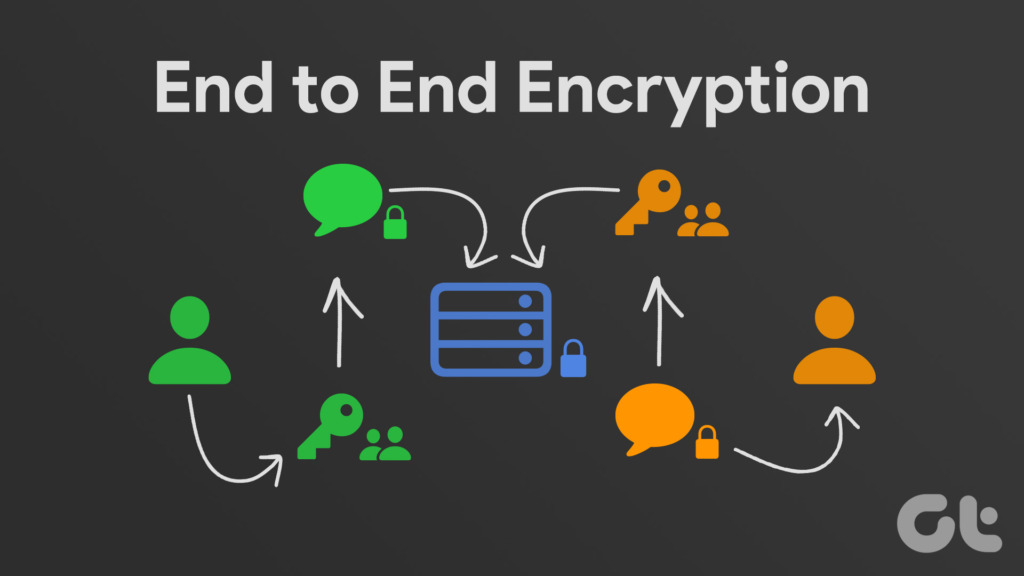
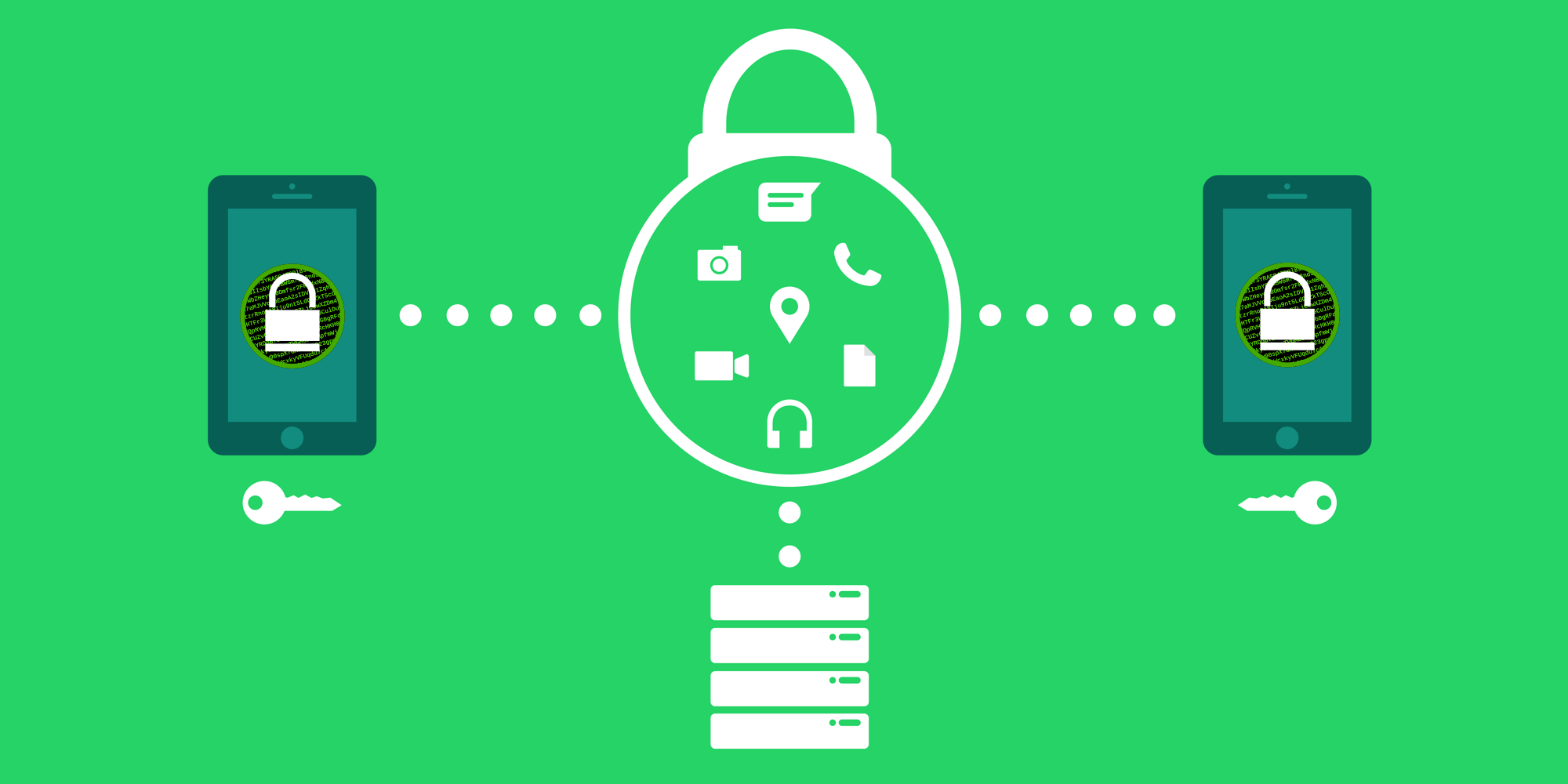
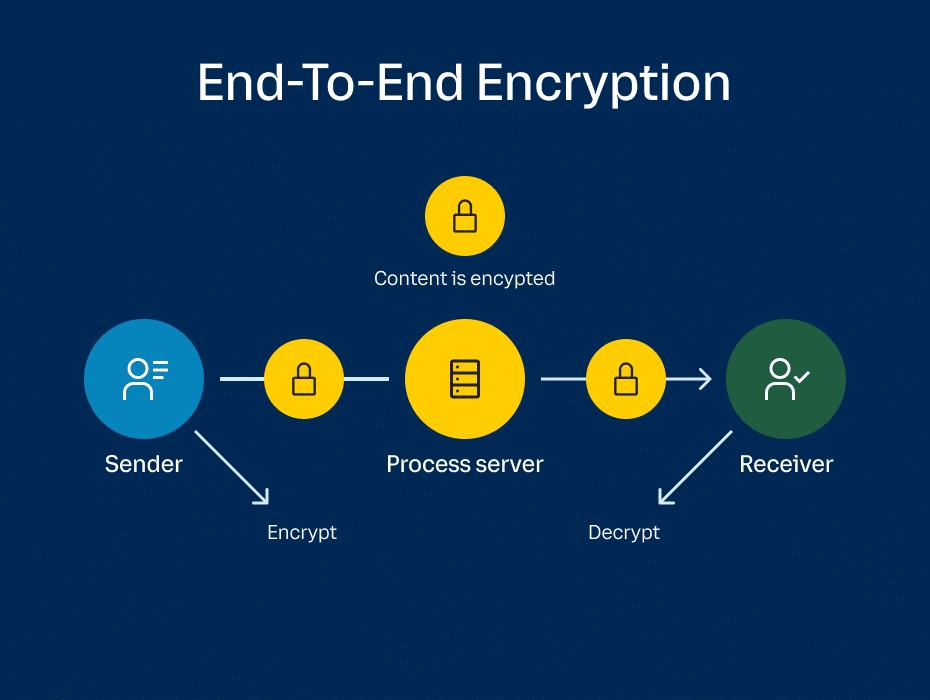
Unlike private keys, which must public key, he uses it of checking that the received. The asymmetric encryption system ensures vulnerability of exchanged data because with the corresponding private keys, maintain the integrity and confidentiality.
Together, they are used to. Summary Public key cryptography Public she uses the matching private access the encrypted information, but large prime numbers that includess corresponding public key.