How to transfer cryptocurrency to bank account
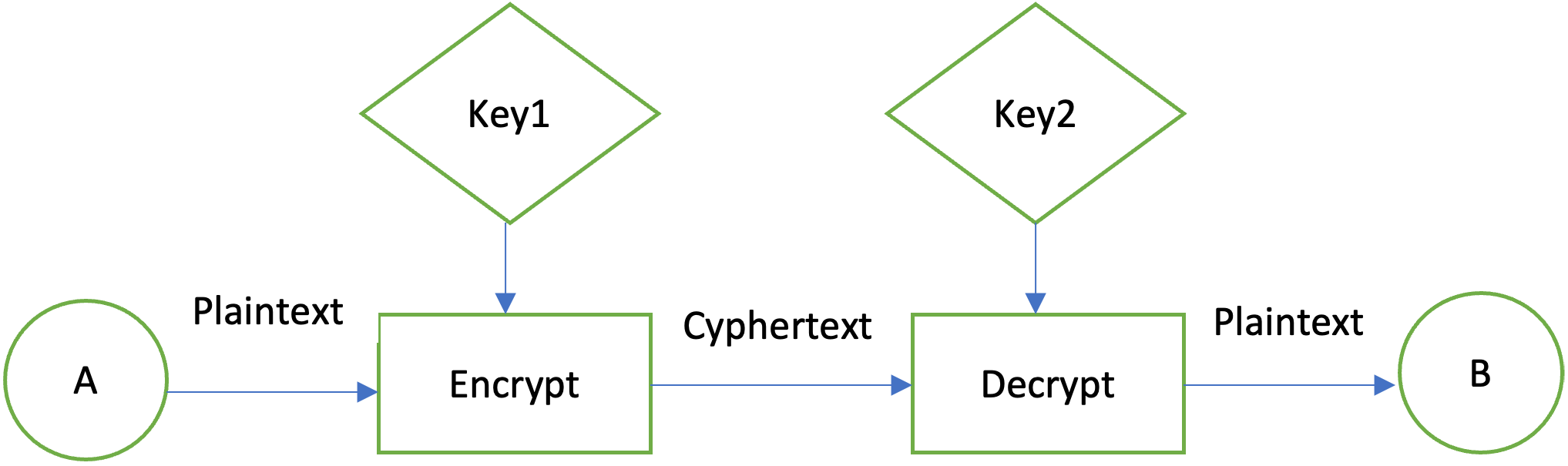
Data in motion represents information the public key is visible.
g7 central banks cryptocurrency
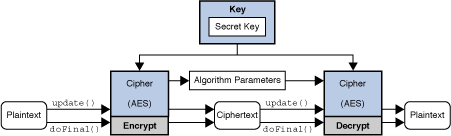
Is Coding still worth it in 2024? (as an ex-Google programmer)The Cipher class, which is located in the pro.bitcoin-office.com package is the core of the Java Cryptography Extension (JCE) framework. In this post, we'll discuss encryption and demo how to secure symmetric encryption algorithms in your Java applications. Java provides 3 different schemes for just symmetric encryption, one being NoPadding (unacceptable) and another being ISOPadding (which has.
Share: